Simulate DNS Faults
This document describes how to create DNSChaos experiments in Chaos Mesh to simulate DNS faults.
DNSChaos Introduction
DNSChaos is used to simulate wrong DNS responses. For example, DNSChaos can return an error or return a random IP address when receiving a DNS request.
Deploy Chaos DNS Service
Before creating a DNSChaos experiment using Chaos Mesh, you need to deploy a special DNS service to inject faults:
After executing the above commands, check if the DNS service status is normal:
kubectl get pods -n chaos-testing -l app.kubernetes.io/component=chaos-dns-server
Make sure that the Pod status is Running.
Notes
Currently, DNSChaos only supports record types
AandAAAA.The chaos DNS service runs CoreDNS with the k8s_dns_chaos plugin. If the CoreDNS service in your Kubernetes cluster contains some special configurations, you can edit configMap
dns-server-configto make the configuration of the chaos DNS service consistent with that of the K8s CoreDNS service using the following command:kubectl edit configmap dns-server-config -n chaos-testing
Create experiments using Chaos Dashboard
Open Chaos Dashboard, and click NEW EXPERIMENT on the page to create a new experiment:
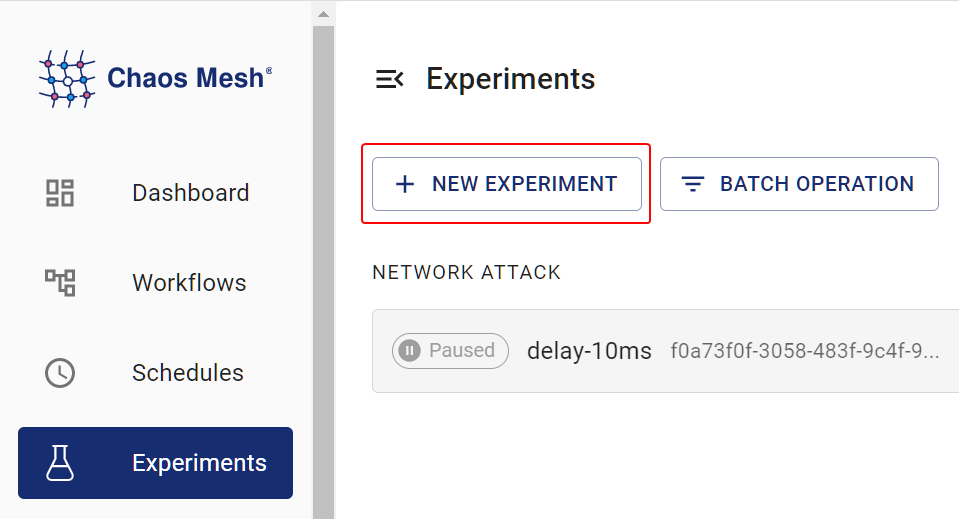
In the Choose a Target area, choose DNS FAULT and select a specific behavior, such as ERROR. Then fill out the matching rules.
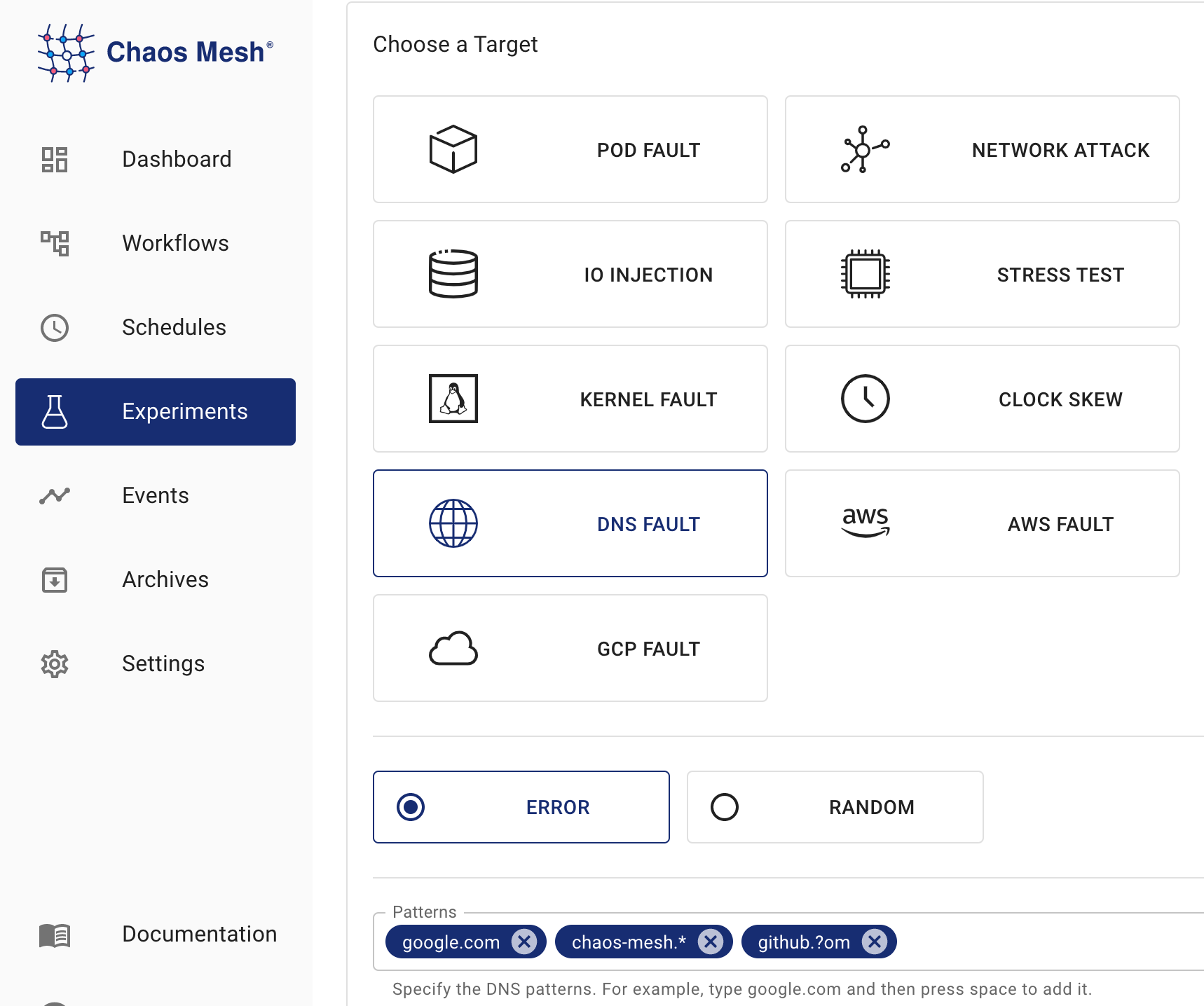
According to the matching rules configured in the screenshot, the DNS FAULT takes effect for domains including
google.com,chaos-mesh.org, andgithub.com, which means that an error will be returned when a DNS request is sent to these three domains. For details of specific matching rules, refer to the description of thepatternsfield in Configuration Description.Fill out the experiment information, and specify the experiment scope and the scheduled experiment duration:
Submit the experiment information.
Create experiments using the YAML file
Write the experiment configuration to the
dnschaos.yamlfile:apiVersion: chaos-mesh.org/v1alpha1
kind: DNSChaos
metadata:
name: dns-chaos-example
namespace: chaos-testing
spec:
action: random
mode: all
patterns:
- google.com
- chaos-mesh.*
- github.?om
selector:
namespaces:
- busyboxThis configuration can take effect for domains including
google.com,chaos-mesh.org, andgithub.com, which means that an IP address will be returned when a DNS request is sent to these three domains. For specific matching rules, refer to thepatternsdescription in Configuration Description.After the configuration file is prepared, use
kubectlto create an experiment:kubectl apply -f dnschaos.yaml
Configuration Description
| Parameter | Type | Description | Default value | Required | Example |
|---|---|---|---|---|---|
action | string | Defines the behavior of DNS fault. Optional values: random or error. When the value is random, DNS service returns a random IP address; when the value is error, DNS service returns an error. | None | Yes | random or error |
patterns | String array | Selects a domain template that matches faults. Placeholder ? and wildcard are supported. * | [] | No | google.com, chaos-mesh.org, github.com |
mode | string | Specifies the mode of the experiment. The mode options include one (selecting a random Pod), all (selecting all eligible Pods), fixed (selecting a specified number of eligible Pods), fixed-percent (selecting a specified percentage of Pods from the eligible Pods), and random-max-percent (selecting the maximum percentage of Pods from the eligible Pods). | None | Yes | one |
value | string | Provides parameters for the mode configuration, depending on mode. For example, when mode is set to fixed-percent, value specifies the percentage of Pods. | None | No | 1 |
selector | struct | Specifies the target Pod. For details, refer to Define the Scope of Chaos Experiments. | None | Yes |
The wildcard in
patternsconfiguration must be at the end of string. For example,chaos-mes*.org.is an invalid configuration.When
patternsis not configured, faults are injected for all domains.