Chaos Dashboard
Chaos Dashboard is a one-step web UI for managing, designing, and monitoring chaos experiments on Chaos Mesh. This document provides a step-by-step introduction on how to use Chaos Dashboard.
Install Chaos Dashboard
You can install Chaos Mesh with Chaos Dashboard by executing the command below:
If you have already installed Chaos Mesh, upgrade it by executing:
Enable/Disable security mode
Chaos Dashboard supports a security mode, which requires users to login with a token generated by Kubernetes. Each token is linked to a service account. You can only perform operations within the scope as allowed by the role that is associated with the service account.
The security mode is enabled by default if you install via Helm. You can disable it by executing:
Note:
- For actual testing scenarios, we strongly recommend that you enable the security mode.
- The security mode is disabled if you install Chaos Mesh by
install.sh, which is suitable for trying Chaos Mesh out.
Access Chaos Dashboard
A typical way to access Chaos Dashboard is to use kubectl port-forward:
kubectl port-forward -n chaos-testing svc/chaos-dashboard 2333:2333
Now you should be able to access http://localhost:2333 in the browser.
Log In
By default, the security mode is enabled when using helm to install Chaos Mesh, and you will need to log in Chaos Dashboard with an account Name and Token. This section introduces how to create the account and the token. You can skip this step if you have disabled the security mode.
Create the account
Chaos Dashboard supports Role-Based Access Control (RBAC).
Note:
- If you want to create the account later and start using Chaos Dashboard quickly, you can use the token of Chaos Mesh. Get the token by executing the command:
kubectl -n chaos-testing describe secret $(kubectl -n chaos-testing get secret | grep chaos-controller-manager | awk '{print $1}'), and then you can go to Fill in directly.
To create the account:
Create the
Role. Here are sample role configurations that you can choose from and edit to meet your specific requirement. You need to save the configuration to an YAML file, and then usekubectl apply -f {YAML-File}to create it.Cluster Manager
This role has administrative permissions on chaos experiments under all namespaces in the Kubernetes cluster, including creating, updating, archiving, and viewing chaos experiments.
Sample configuration file:
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: cluster-role-manager
rules:
- apiGroups: ['']
resources: ['pods', 'namespaces']
verbs: ['get', 'list', 'watch']
- apiGroups:
- chaos-mesh.org
resources: ['*']
verbs:
- get
- list
- watch
- create
- update
- patch
- deleteCluster Viewer
This role has permission to view chaos experiments under all namespaces in the Kubernetes cluster.
Sample configuration file:
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: cluster-role-viewer
rules:
- apiGroups: ['']
resources: ['pods', 'namespaces']
verbs: ['get', 'list', 'watch']
- apiGroups:
- chaos-mesh.org
resources: ['*']
verbs:
- get
- list
- watchNamespace Manager
This role has administrative permissions on chaos experiments under a specified namespace in the Kubernetes cluster, including creating, updating, archiving, and viewing chaos experiments.
The sample configuration file is as follows:
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: namespace-test-role-manager
namespace: test
rules:
- apiGroups: ['']
resources: ['pods', 'namespaces']
verbs: ['get', 'list', 'watch']
- apiGroups:
- chaos-mesh.org
resources: ['*']
verbs:
- get
- list
- watch
- create
- update
- patch
- deleteNamespace Viewer
This role has access to the chaos experiment under a specified namespace in the Kubernetes cluster.
Sample configuration file:
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: namespace-test-role-viewer
namespace: test
rules:
- apiGroups: ['']
resources: ['pods', 'namespaces']
verbs: ['get', 'list', 'watch']
- apiGroups:
- chaos-mesh.org
resources: ['*']
verbs:
- get
- list
- watch
Create a
ServiceAccount, and bind it with a specificRole. Refer to RBAC for more details. Here are sample configurations that you can choose from and edit to meet your specific requirement. You need to save the configuration to an YAML file, and then usekubectl apply -f {YAML-File}to create it.Create a ServiceAccount and bind cluster role
Create a ServiceAccount and bind it with the role
Cluster ManagerorCluster Viewer.Sample configuration file:
kind: ServiceAccount
apiVersion: v1
metadata:
name: account-cluster-manager # use "account-cluster-viewer" for viewer
namespace: chaos-testing
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: bind-cluster-manager # use "bind-cluster-viewer" for viewer
subjects:
- kind: ServiceAccount
name: account-cluster-manager # use "account-cluster-viewer" for viewer
namespace: chaos-testing
roleRef:
kind: ClusterRole
name: cluster-role-manager # use "cluster-role-viewer" for viewer
apiGroup: rbac.authorization.k8s.ioCreate a ServiceAccount and bind namespace role
Create a ServiceAccount and bind it with the role
Namespace ManagerorNamespace Viewer.Sample configuration file:
kind: ServiceAccount
apiVersion: v1
metadata:
name: account-namespace-test-manager # use "account-namespace-test-viewer" for viewer
namespace: test
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: bind-namespace-test-manager # use "bind-namespace-test-viewer" for viewer
namespace: test
subjects:
- kind: ServiceAccount
name: account-namespace-test-manager # use "account-namespace-test-viewer" for viewer
namespace: test
roleRef:
kind: Role
name: namespace-test-role-manager # use "namespace-test-role-viewer" for viewer
apiGroup: rbac.authorization.k8s.io
Get the token
The token is generated by Kubernetes. To get a token for the ServiceAccount created above, run command below:
kubectl -n ${namespace} describe secret $(kubectl -n ${namespace} get secret | grep ${service-account-name} | awk '{print $1}')
Note:
- You need to replace the
${namespace}and${service-account-name}with the actual value. For example, executing commandkubectl -n chaos-testing describe secret $(kubectl -n chaos-testing get secret | grep cluster-role-manager | awk '{print $1}')to get the token ofcluster-role-manager.
Refer to getting-a-bearer-token for more details.
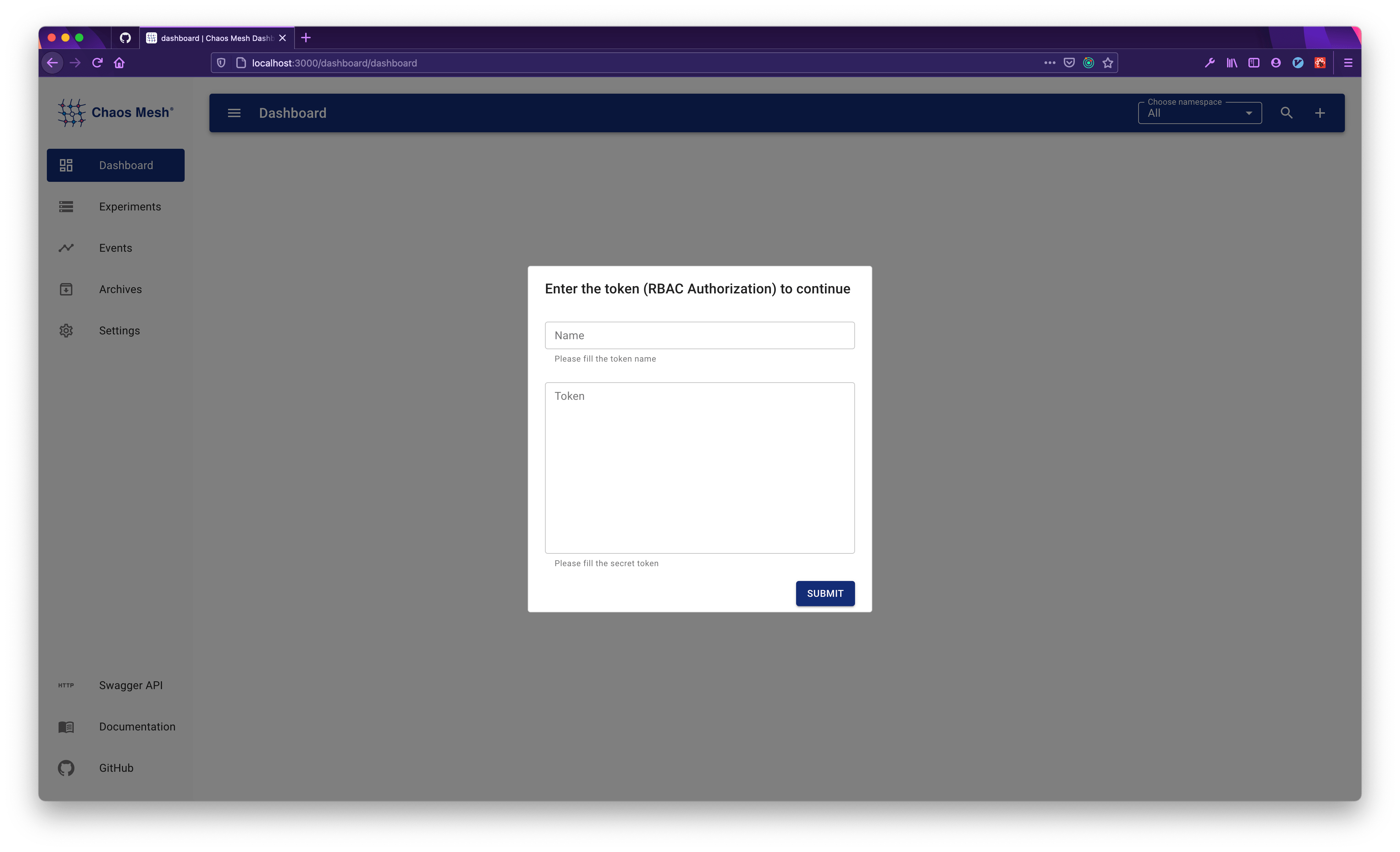
Fill in
With the token generated, you need to identify it with a Name. A meaningful name is recommended, for example, Cluster-Manager, to indicate that the token has permissions managed chaos experiments in the cluster.
Fill in the form with Name and Token:
Create a chaos experiment
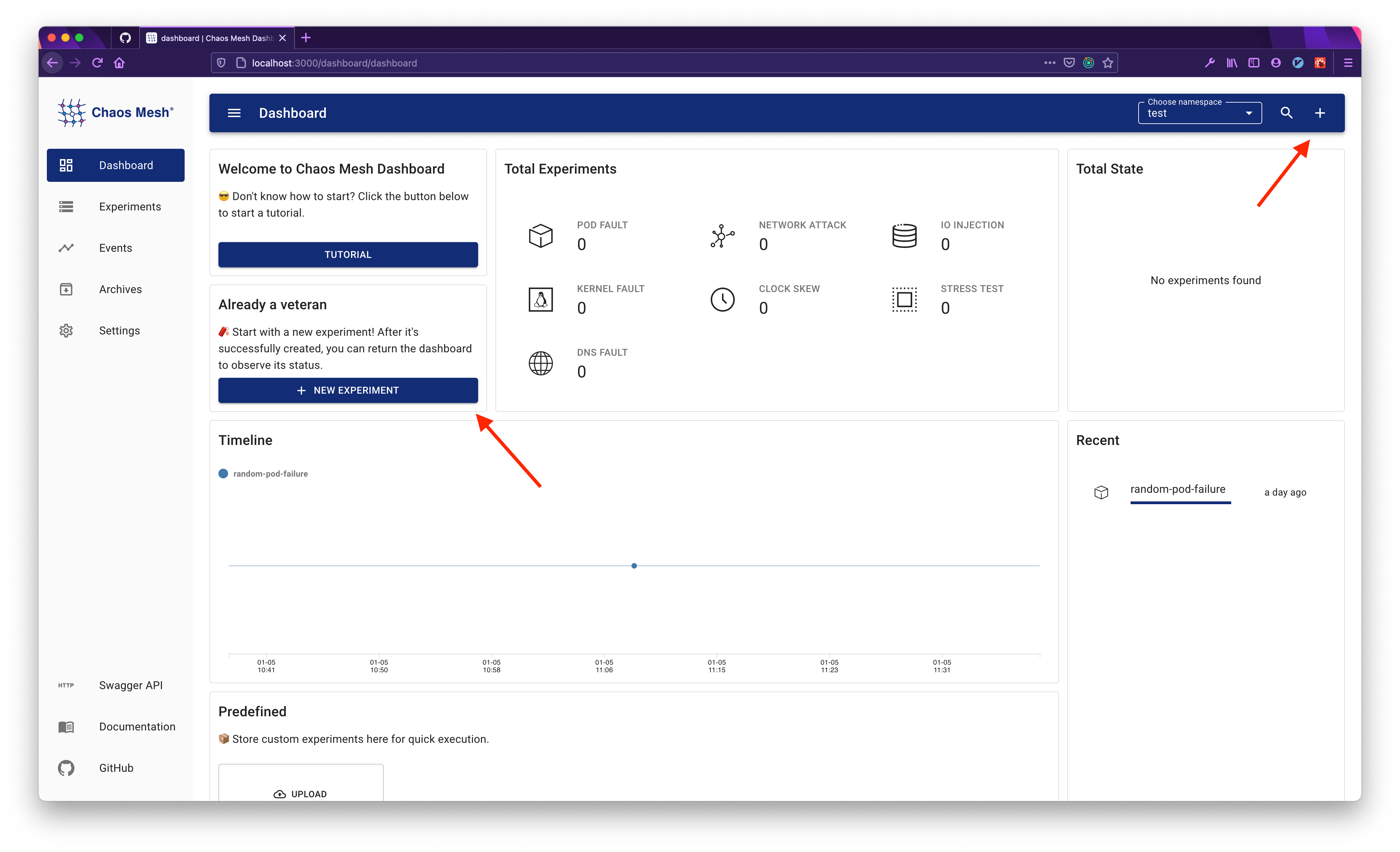
To create a chaos experiment on Chaos Dashboard:
Click the NEW EXPERIMENT button to create a new chaos experiment:
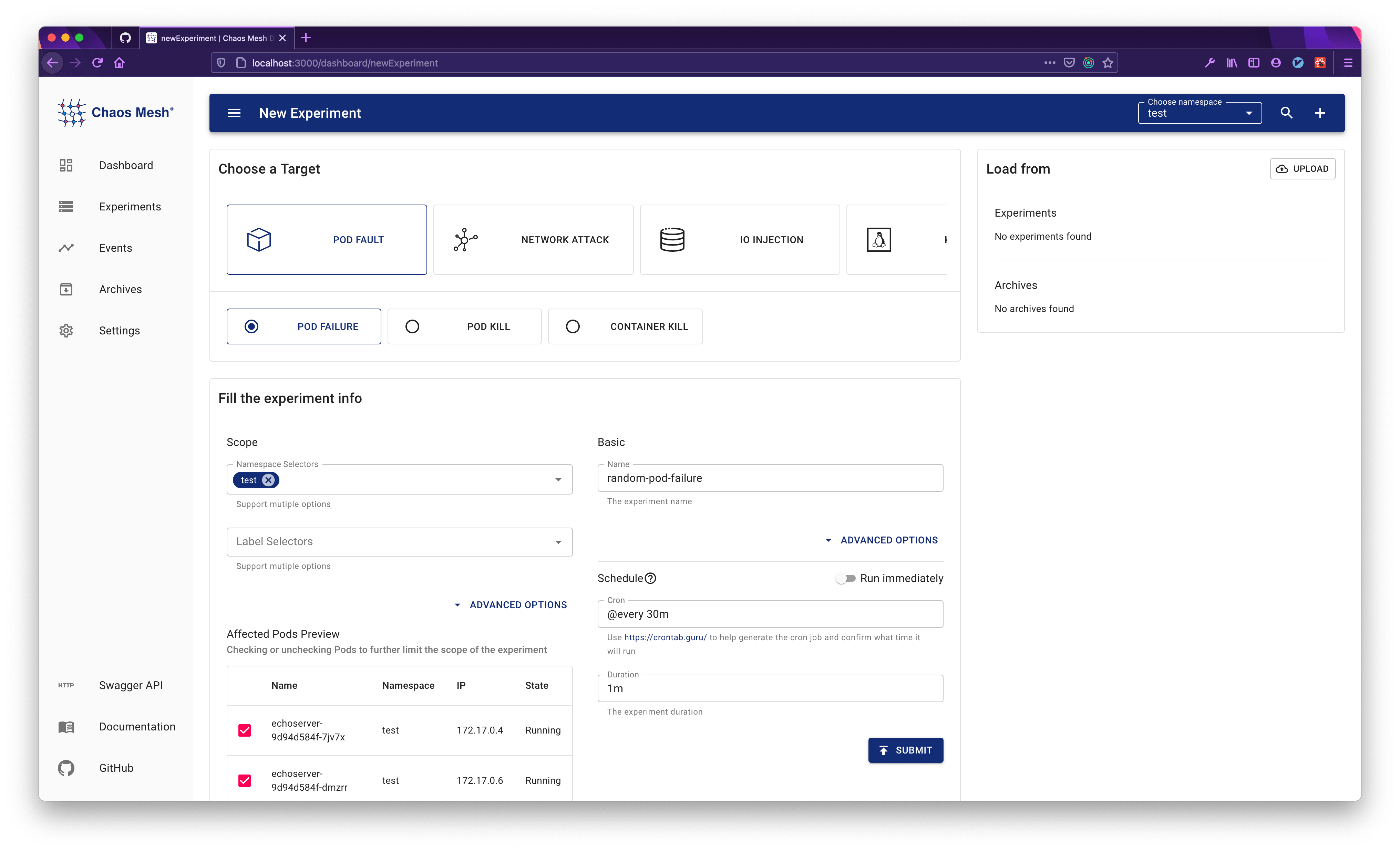
Configure the chaos experiment, including the experiment type, name, scheduling information, etc.
Manage a chaos experiment
To manage a specific chaos experiment:
Click the Experiments button to view all the chaos experiments.
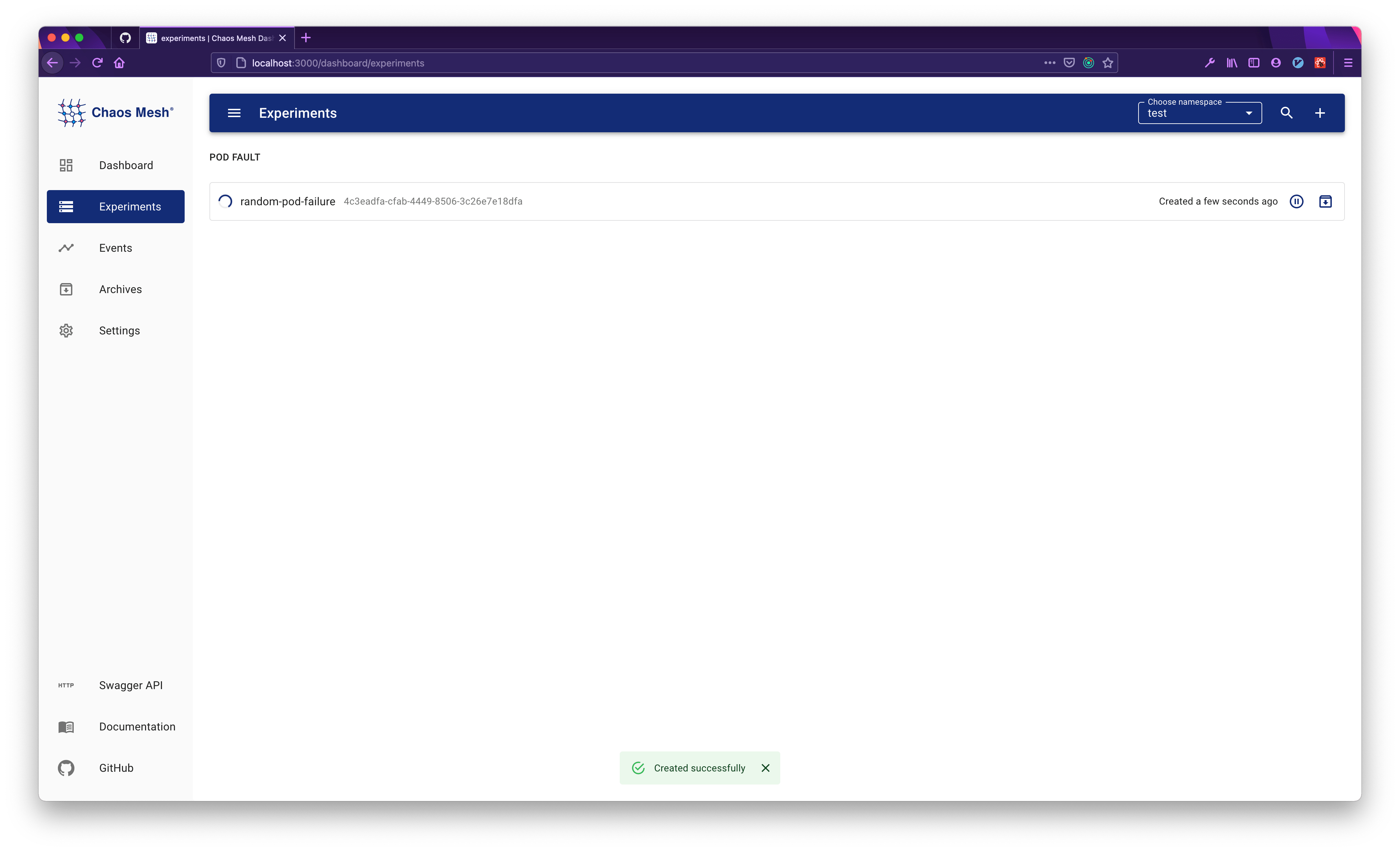
Choose the target experiment to view the detail, archive, pause or update.
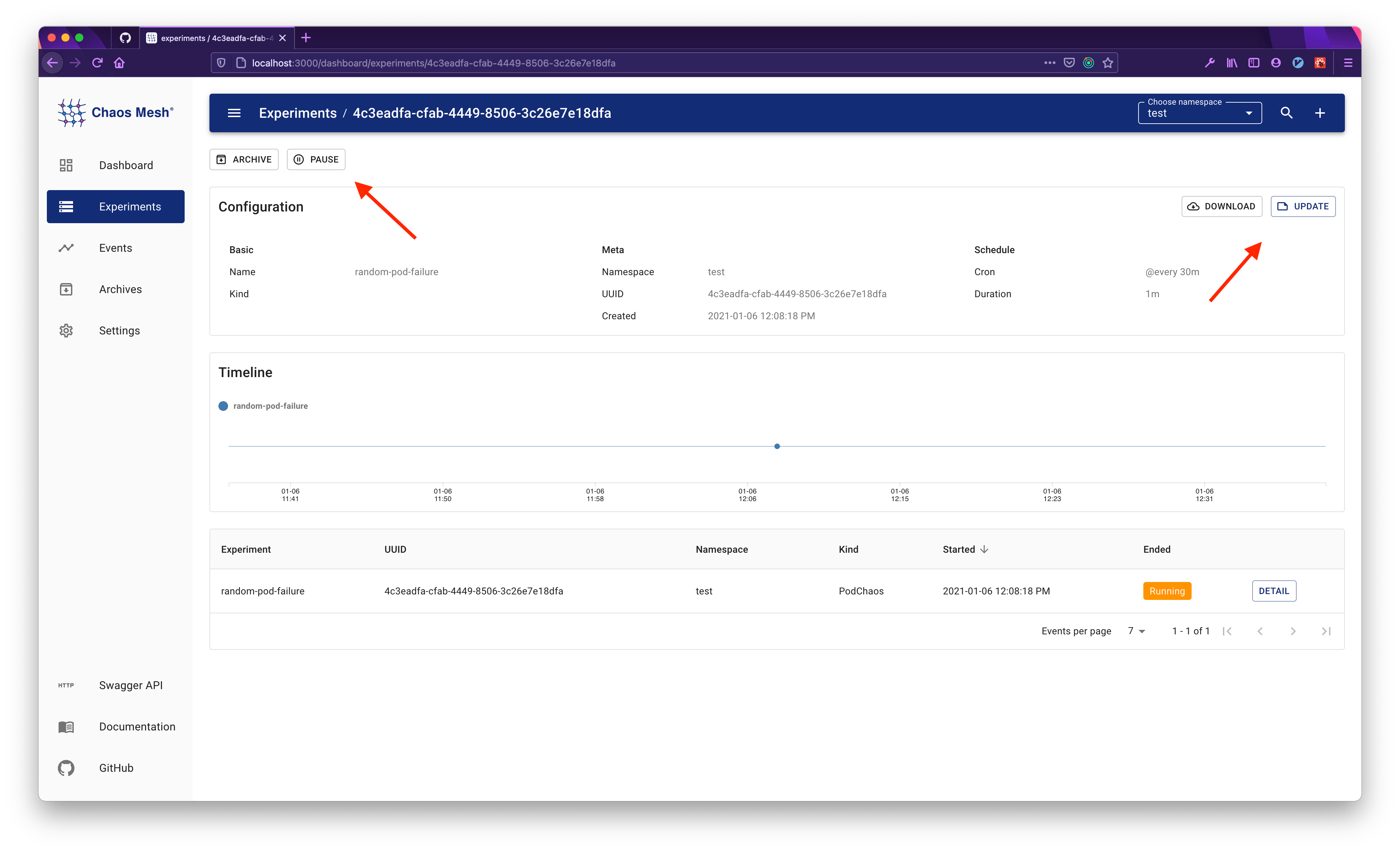
Quick glance
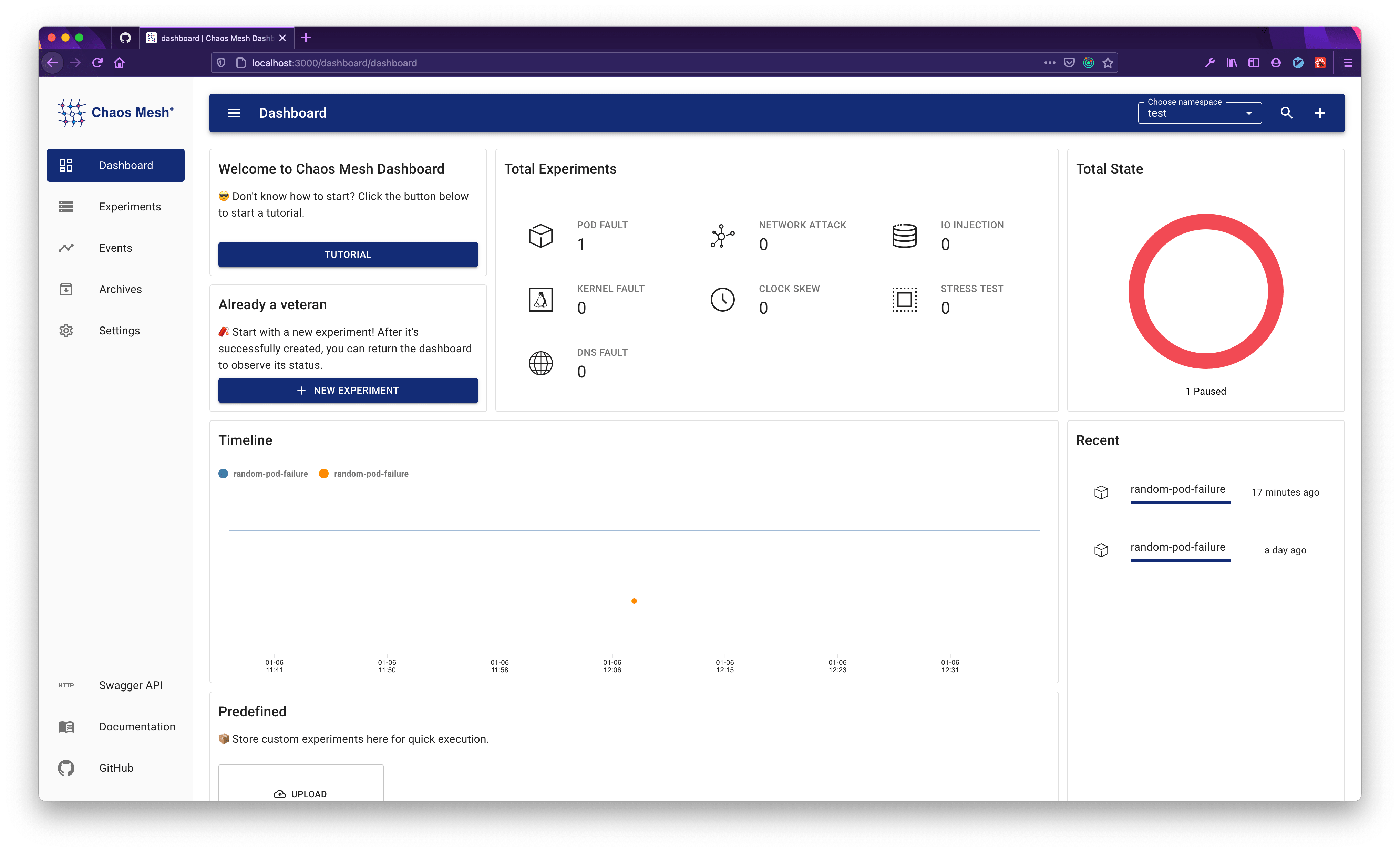
Through the steps just now, you already know how to create an experiment and view its detail. But this is only one of the main features of the dashboard.
Next, you can click the TUTORIAL button on the homepage to learn about all the features of the dashboard.
Manage existing tokens
To create and manage existing tokens:
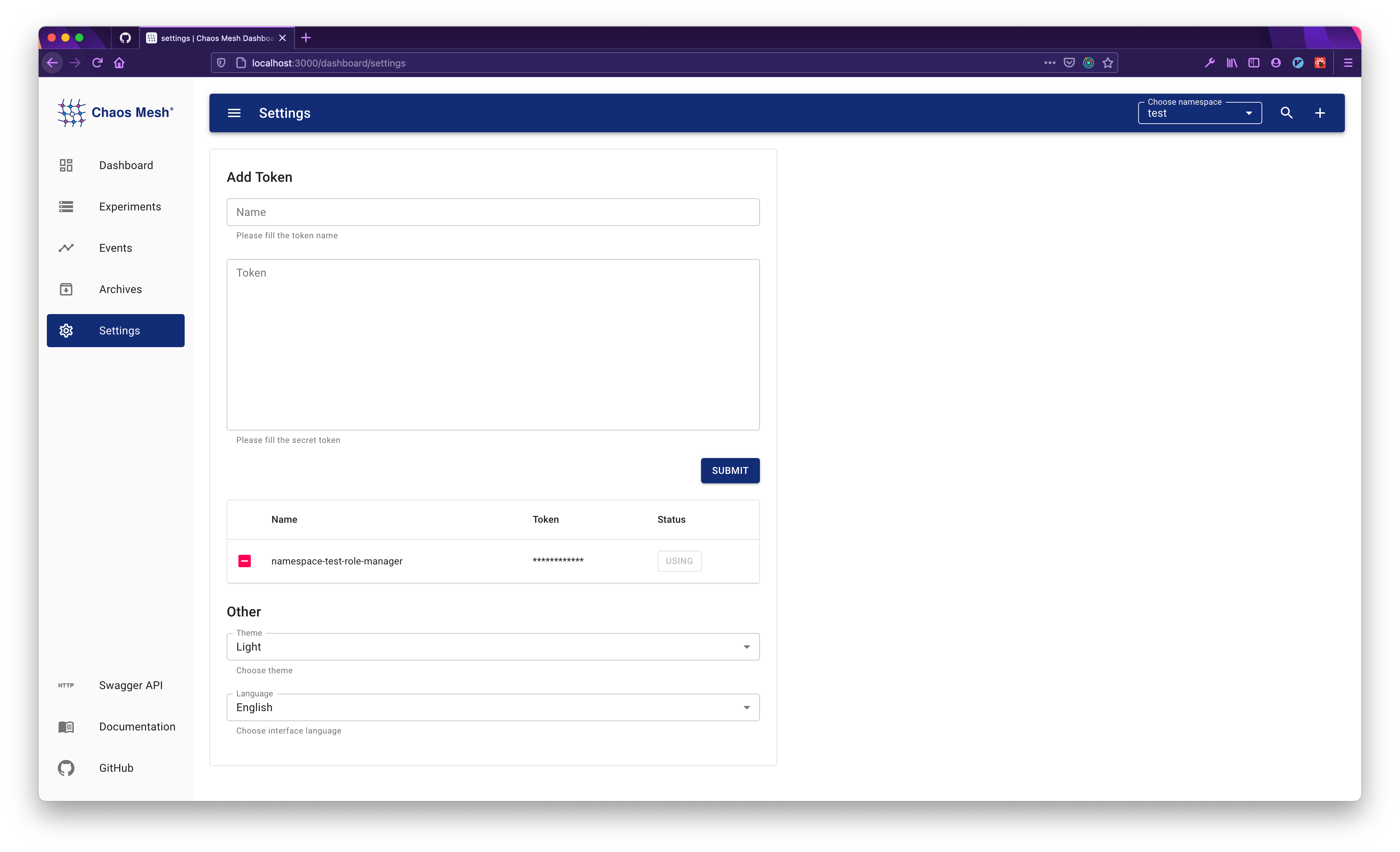
Note:
If
dashboard.securityMode=falseis set, this section will be invisible.